Abstract
Terrorist acts continue to be a serious problem for Russia, which leads to serious life and material losses, and also has a strong pressure on the government. Types of objectives that are attacked are becoming more and more diverse. Public transport facilities such as railway stations and airports, communication networks, government buildings, public facilities, private businesses, enterprises and many others are at risk of attack. The article examines objective types that terrorists prefer. Objective risk analysis is proposed to use a three-dimensional model that takes into account threat probability, objective vulnerability, and severity of consequences. The article also provides risk calculation and assessment of risk level with a fuzzy synthesis method, as well as two examples of risk assessment that are intended to prove the feasibility of the model. The study used the data from the Global Terrorism Database for six types of objectives that were attacked in the Russian Federation from 1994 to 2017. To analyze the characteristics of a large amount of data, statistical and approximation methods were used, as well as methods of mathematical modeling and risk assessment. The study can help identify potential objectives, assess risk levels and preparation for emergency management. In addition, the paper concludes that in future studies it is necessary to improve assessment method and a classification standard of risk indicators, while optimizing the risk assessment process and paying more attention to the research of specialists in the field of terrorism.
Keywords: Terrorismrisk of terrorist actsrisk assessmentmodeldiversity of objectives
Introduction
Terrorism continues to evolve and expand around the world. As one of the types of technological events, as soon as a terrorist attack occurs, it can lead to serious casualties and material losses, influence on public opinion and put much pressure on the government. Today the types of objectives that are being attacked are becoming more and more diverse. Public transport facilities, such as railway stations and airports, communication networks, government buildings, public facilities, private businesses, enterprises and many others are at risk of terrorism. If we can identify potential objectives that could be attacked by terrorists, assess the level of risk and prepare a management plan in advance, this will be important to crises management.
Problem Statement
Russian and foreign scientists conduct much research in this area. Wang and Zhuang (2012) studied the types and nature of terrorist attacks that occurred in Russia. Santifort, Sandler, and Patrick (2015) presented points of change in types of attacks and their drivers based on a variety of targets for terrorist attacks. A study by Chatteijee and Abkowitz (2011) provides a methodology to model regional terrorism. Major (2002) first built a quantitative risk model for terrorism based on the game theory. Woo (2002) developed a process to quantify terrorism risk. For the first time, Mohtadi and Murshid (2009) applied a value approach to assess the risk of catastrophic terrorism. Akhmetkhanov, Dubinin, and Kuksova (2018) stated in the paper the process of assessing the risk of terrorist attacks on urban and industrial facilities. Russian scientists Makhutov and Reznikov (2015) studied the methods to assess the risk of terrorist acts at underground stations and technological facilities.
Research Questions
However, in Russia there are still no studies on the diversity of attacked objectives, and existing risk assessment models refer only to one type of objects and are not universal. Therefore, to solve this problem, this article first examines objective diversity regarding the types of objectives and diversity index. The paper provides the analysis of objective risk through the most common three-dimensional model, which consists of threat possibility (likelihood of attack), objective vulnerability (success of attack), and severity of consequences (damage). Finally, the article calculates the risk and estimates the level of risk with a fuzzy synthesis method, and also provides an example of risk assessment, which is intended to prove the feasibility of using the model.
Purpose of the Study
The purpose of this paper is to identify the main methods to assess the risks of terrorist acts against potential objectives of various types, which may help to create a risk management plan for the most significant objects in advance and will be important for responding to crises associated with terrorism and managing their consequences.
Research Methods
Statistical and approximation methods are widely used to analyze the characteristics of large amounts of data (Ayyub, 2008; Slovic, 2002). The article also uses this approach. The data was taken from Global Terrorism Database. For a simple study, we will divide objective types into six types from 1994 to 2017 in Russia: government, police and army, infrastructure, enterprises, individuals and property, as well as social institutions indicated in Fig.
Findings
Since urban areas have widespread infrastructure such as transport, water supply systems, electricity, communications networks, telecommunications, etc., to which terrorists have easy access, the cumulative number of attacks against them has remained relatively stable since 2015. The social infrastructure represented by educational institutions (schools and kindergartens), hospitals and clinics, editorial boards of the media, NGOs and charitable organizations, as well as other socially significant facilities, is particularly vulnerable. The attack on such objects, which affects the normal functioning of the city, can cause widespread public panic. The cumulative number of attacks by businesses and individuals in the past few years is lower than the infrastructure, but still growing. These two types of objectives, to which terrorists have easy access, and whose employees have lower awareness of countering terrorism, have recently become highly favored targets.
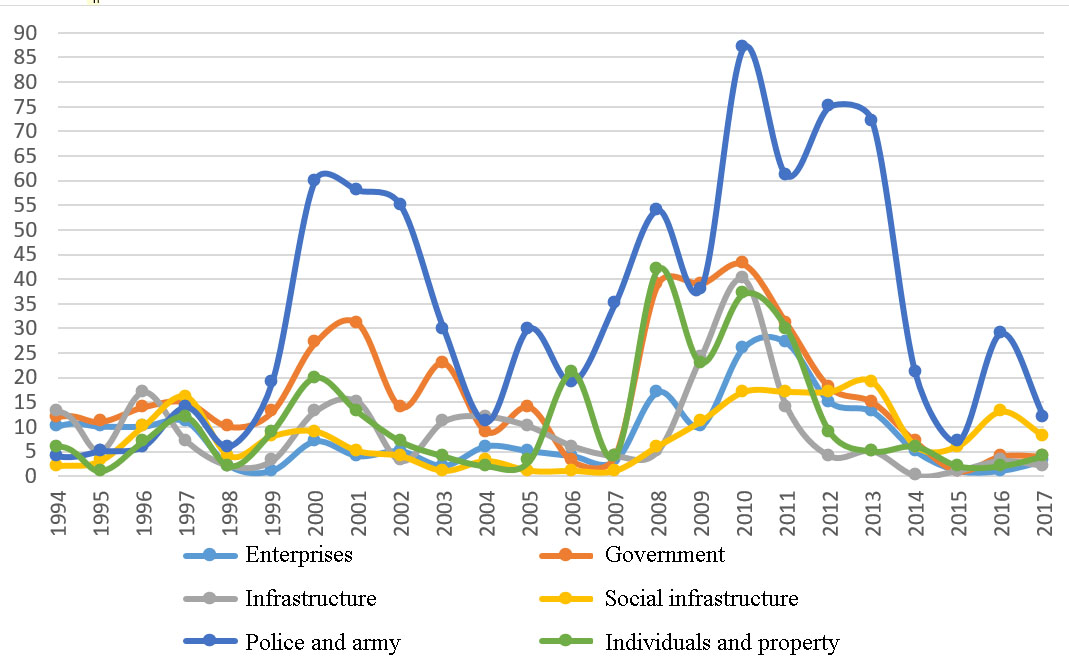
In the overwhelming majority, attacks occur precisely at the police stations and the army. Attacks on these objectives put a lot of pressure on the government and reduce public confidence in law and order, because it indicates their vulnerability or “helplessness” to terrorists (Table
In short, social infrastructure, as well as the police and the army are the main objectives for terrorists. As can be seen from Fig.
Si is the proportion of total attacks on objective type i when measuring objective diversity; n is the total number of objective types; the measure of diversity varies from 0 to 1, with 0 indicating no diversity and 1 indicating complete diversity. N is the number of targeted attack types. Fig.
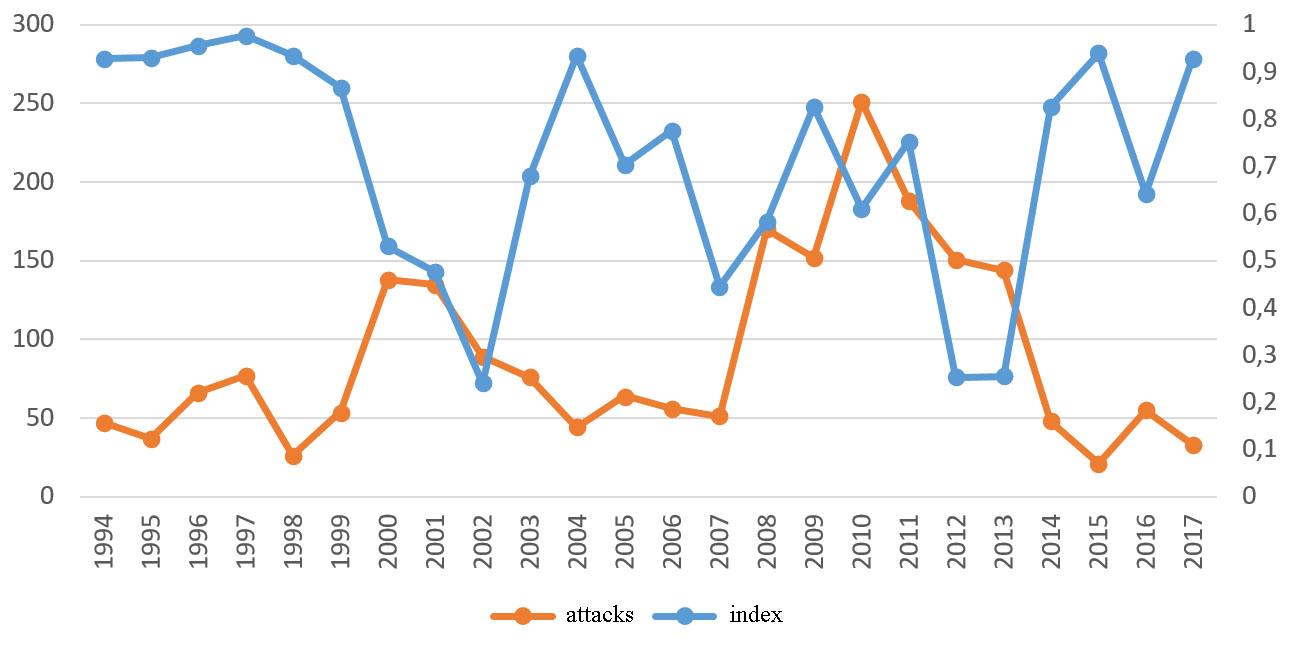
Fig.
(1) Confirmation of the set of risk factors U = {u1, u2, ..., un} and the set of solutions V = {v1, v2, ..., vn}. U = {threat capability, target vulnerability, severity}, V = {very high, high, medium, low};
(2) Weight calculation of each factor with the method of expert assessments and analytical hierarchical process: W = {w1, w2, ..., wn},
(3) Construction of the estimated set R. The choice of the coefficient i in the multiplier U and the estimate of the degree of its belonging rij to the element j from the set of solutions V in the form of Table
Comprehensive assessment matrix
(4) Risk assessment with an equation B = W*R, then we know risk matrix RD = {r1, r2, r3, r4} and calculate risk with the formula ScoreR = (r1, r2, r3, r4)*(88.5, 62.5, 37.5, 12.5)-1, and ri = (i=1,2,3,4) represents the degree of risk distribution of each risk level. The risk level is shown in Table
Practical example
(1) A business building with 20 floors located in the regional city of an unstable region (for example, Russian republics of the North Caucasus), which accommodates many workers. This objective has never been attacked by terrorists before, and threat attack was not identified by the security services. However, the building has taken some security measures.
(2) A city police station located in an unstable region in which there are several police officers with weapons, experience and skills. A similar objective had previously been attacked by terrorists, so the threat attack was determined.
In the example, the set of factors is U = {probability of attack, objective vulnerability, severity of consequences}, and the set of judgments is V = {very high, high, medium, low}. The results of risk assessment are shown in Table
Based on Table
Conclusion
In this paper, we studied the diversity of objectives for terrorist attacks, which helps to identify the types of objectives that terrorists recently prefer. Then, the analysis of objective risk of a three-dimensional model was presented, taking into account threat probability, vulnerability of objectives and consequences. Finally, risk level was assessed with a fuzzy decision-making method. Two examples of risk analysis of business and police objectives were cited. The study can help identify potential objectives, assess objective risk levels and prepare for emergency management. However, research still has some problems. In future studies, it is necessary to improve the assessment method and classification standard of risk indicators, while optimizing the risk assessment process and paying more attention to the research of specialists in the field of terrorism.
References
- Akhmetkhanov, R. S., Dubinin, Е. F., & Kuksova, V. I. (2018). The use of fuzzy methods of risk assessment in the presence of terrorist threats. Security and Emergency, 1, 38–55.
- Ayyub, B. M. (2008). Terrorism risk: characteristics and features. Wiley Handbook of Science and Technology for Homeland Security. John Wiley & Sons, Inc.
- Chatteijee, S., & Abkowitz, M. D. (2011). A methodology for modeling regional terrorism risk. Risk Analysis, 31(7), 1133–1140.
- Cox, L. A. (2008). Some Limitations of Risk = Threat × Vulnerability × Consequence for Risk Analysis of Terrorist Attacks. Risk Analysis, 28, 1749–1761.
- Garrick, J. B., (2004). Confronting the risks of terrorism: Making the right decisions. Reliability Engineering and System Safety, 86(2), 129–176.
- Major, J. A. (2002). Advanced techniques for modeling terrorism risk. Journal of Risk Finance, 4(1), 215–241.
- Makhutov, N. А., & Reznikov, D. О. (2015). Scientific basis to assess terrorist risks and terrorist threats for comprehensive technical systems. Security and Emergency, 2, 53–74.
- Mohtadi, H., & Murshid, A. P. (2009). Risk of catastrophic terrorism: an extreme value approach. Journal of Applied Econometrics, 24(4), 537–559.
- Renfroe, N. A, & Smith, J. L. (2002). Threat/Vulnerability Assessments and Risk Analysis. Cambridge: Applied Research Associates Inc.
- Santifort, C., Sandler, T., & Patrick, T. B. (2015). Terrorist attack and target diversity: Change points and their drivers. Journal of peace research, 50(1), 75–90.
- Slovic, P. (2002). Terrorism as a Hazard: A new species of trouble. Risk Analysis, 22(3), 425–426.
- Wang, Y. F., & Zhuang, H. W. (2012). Russia suffered terrorist attack target types change analysis. Siberian studies, 39(3), 34–36.
- Willis, H. (2005). Estimating Terrorism Risk. Santa Monica: Rand Corporation.
- Woo, G. (2002). Quantitative terrorism risk assessment. Journal of Risk Finance, 4(1), 7–14.
Copyright information

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
About this article
Publication Date
28 December 2019
Article Doi
eBook ISBN
978-1-80296-075-4
Publisher
Future Academy
Volume
76
Print ISBN (optional)
-
Edition Number
1st Edition
Pages
1-3763
Subjects
Sociolinguistics, linguistics, semantics, discourse analysis, science, technology, society
Cite this article as:
Novikov*, A. (2019). Risk Assessment Of Terrorist Acts Based On Study Of Diversity Of Objectives. In D. Karim-Sultanovich Bataev, S. Aidievich Gapurov, A. Dogievich Osmaev, V. Khumaidovich Akaev, L. Musaevna Idigova, M. Rukmanovich Ovhadov, A. Ruslanovich Salgiriev, & M. Muslamovna Betilmerzaeva (Eds.), Social and Cultural Transformations in the Context of Modern Globalism, vol 76. European Proceedings of Social and Behavioural Sciences (pp. 2482-2490). Future Academy. https://doi.org/10.15405/epsbs.2019.12.04.332
