Abstract
Nowdays, integrity and trust is raised and expanded. In making sure that the system to be successful, these two elements are needed. It is the main task as a service provider to guarantee a system that is always free from any errors. Due to this reason, a system called SAFELY IN, SECURELY OUT SYSTEM (E-SISO) is created. E-SISO is a security system focusing on thumbprint method that is specially created for Immigration Department of Malaysia in convincing the public that they are “Doing It Right the First Time”. E-SISO is concentrating into solving and diminishing any arise issues during the arresting procedures of PATI up to their releasing day. The main highlight of E-SISO is the promising process that resulted to zero error. This can only be done when the PATI (suspect or “OKT”) is “Safely In” throughout the whole processes and they are “Securely Out” during releasing day without any complaints for any loss that covering the individuals and their belongings. There are lots of advantages and benefits of E-SISO from being paperless to guaranteeing software interoperability and meeting current standards. As for novelty factor, E-SISO will be the first to be implemented in Immigration Department of Malaysia which can be a model for generalization purposes to other public security departments.
Keywords: E-SISOIntegrityImmigration Department of MalaysiaPATISecuritySystem
Introduction
Current organizations depend on information systems (IS) for their existence; this is because such systems often hold treasured organizational data resources (Cavusoglu et al., 2004; Richardson, 2011; Ifinedo, 2009, 2011, 2012). To protect the main IS assets held in such systems from misuse, abuse and destruction; organizations often utilize a variety of methods such as installing firewalls, updating anti-virus software, backing up their systems, maintaining and restricting access controls, using encryption keys, using surge protectors, and using wide-ranging monitoring systems (Ryan, 2004; Workman, Bommer and Straub, 2008; Lee and Larsen, 2009). However, the said methods offer a technological or technical solution to the problem, and are hardly sufficient in providing total protection of IS organizational resources (Rhodes, 2001; Sasse et al., 2004; Stanton, Stam, Mastrangelo, and Jolton 2005; Herath and Rao, 2009). The implementation of IS need to gain the integrity and trust. These are the main support elements in order to be successful developed systems. As a service provider, it is the main task to guarantee a system that is always free from errors.
Therefore, a system called SAFELY IN, SECURELY OUT SYSTEM (E-SISO) is formed. E-SISO is specially created for Immigration Department of Malaysia in convincing the public that they are “Doing It Right The First Time”. E-SISO is focusing into solving and lessening any arise issues during the arresting procedures of PATI (Illegal immigrants) up to their releasing day. The main highlight of E-SISO is the capable process that resulted to zero error. This can only be done when the PATI is “Safely In” throughout the whole processes and they are “Securely Out” during releasing day without any complaints for any loss that covering the individuals and their belongings. There are many listed advantages and benefits of E-SISO from being paperless to guaranteeing software interoperability and meeting current standards. As for novelty factor, E-SISO will be the first to be implemented in Immigration Department of Malaysia which can be a model for generalization purposes to other public security departments. E-SISO is also enhanced with a thumbprint system that can ensure the reliability and validity of the processes involved are all secured and free from errors. E-SISO will ensure that both parties (the Immigration Department of Malaysia and PATI) are free from any discrimination and lead to justice without prejudice
The issue of illegal immigrant in Malaysia is still popular. In fact, it has been talked since before independence and becomes a major distress for the government to provide them with the basic needs like shelter and other requirements as prescribed by the international law for human rights. It is certainly will acquire additional huge cost in government spending from the taxpayers, in fulfilling the needs of these illegal immigrants. These include the expenditure incurred in retaining them at the detaining centers across the country before being deported to their home country.
Malaysia has been a favorite destination for foreign workers to make a living in this country for several reasons such as geographical factor, shortage of total workforce, government policy etc. Some of the foreign workers hired are legal while others are not. As such, various operations and programs have been taken seriously by the government to reduce the number of illegal immigrant in this country.
This task is under Immigration Department of Malaysia which is under the Ministry of Home Affairs, which provides services to Malaysian Citizens, Permanent Residents and Foreign Visitors.The functions of the department are as follows:
Issuing of passports and travel documents to Malaysian Citizens and Permanent Residents.
Issuing of visas, passes and permits to Foreign Nationals entering Malaysia.
and managing the movement of people at authorised entry and exit points.
Enforcing the Immigration Act 1959/63, Immigration Regulations 1963, Passport Act 1966, Anti-Trafficking in Persons and Anti-Smuggling of Migrants Act 2007 (Amendment 2010).
Problem Statement
Padayachee (2012) suggested a classification for compliant information security behavior by considering extrinsic (e.g. regulatory requirements) and intrinsic (e.g. employee competence, their commitment, ethical values, personality, values and attitude) motivations. A vital conclusion from Ifinedo’s (2012) research is that attitude towards compliance has the greatest effect on information security policy compliance. Similarly, Siponen et al. (2014) claim that employees’ perceived severity, vulnerability, self-efficacy, normative beliefs and attitude have a positive and significant impact on their intention to comply with information security policies and procedures. More recently, Sherif et al. (2015) recommended five variables that could influence information security culture, namely, information security behavior, top management support, security education and awareness, the information security policy and information security acceptance. Therefore, a system need to be developed in order to show that integrity in a system is free from any damages. E-SISO has been established to prove that it supports the integrity in any services offered. With the use of thumb print procedures, barcode scanning tool and online reporting, the services offered by Immigration Department of Malaysia will become more than easy, reliable and lead to justice and fairness.
Research Questions
What are the relevant components or elements that are needed in a trusted system?
How should a process of a system be developed in managing a trusted system?
Purpose of the Study
The importance of E-SISO to community and agencies.
E-SISO is an important to community because it acts as a measurement and proven tool to validate security and proving the value of integrity is equitably practiced in security public department especially Immigration Department of Malaysia. This will raise the value of trust and grow positive relationship not only in the services provided but also to the respective officer in-charge who handled the processes.
Research Methods
Depiction & Explanation of E-SISO.
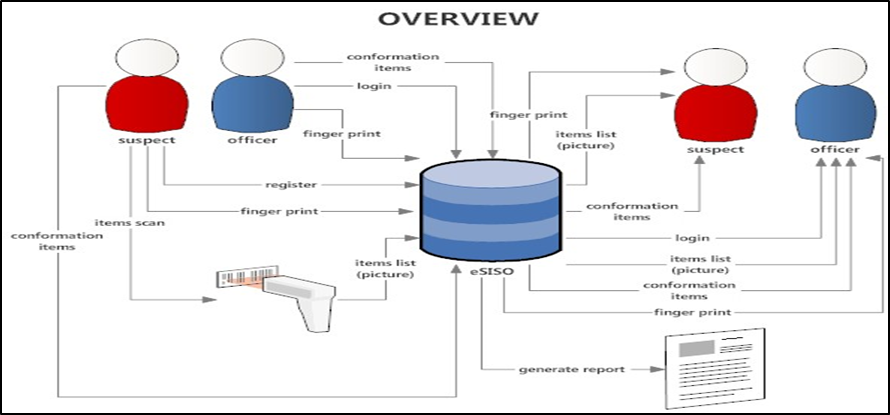
Figure
Findings
Benefits of E-SISO.
There are 10 listed benefits of E-SISO to any public security agencies particularly to the Immigration Department of Malaysia:
Paperless: By using E-SISO, it helps to diminish the use of papers when everything is easily recorded in a system. All manually procedures involved earlier will be stopped and more accurate record will be produced.
Efficient business operation (speed & protection to valuable information): Decentralized filing systems often precipitate time consuming file retrieval. With file situated at different locations it becomes a far more complex task for officers to retrieve files. Officers of Immigration Department of Malaysia will have to spend valuable time contacting colleagues from other departments inquiring after the location of files and will have to then rummage through these often unfamiliar storage rooms.
Reducing disbursement; Keeping pace with the maintenance of several storage sites is likely to be lavish. Firms that use decentralized filing systems are not only more likely to using insufficient sites for document storage but are probably spending more on the preservation of multiple storage sites. A centralized filing system of E-SISO will eliminate the need for replication of filing equipment and conforming security measures. Besides, onsite and offsite centralization both reduce precious office space disbursement.
Increasing safety: Having files in one site is likely to endorse greater information security in your workstation. Centralized filing offers only one point of access which can be easily supervised and restricted. A data breach could have devastating repercussions for Immigration Department of Malaysia. Therefore E-SISO is a need.
Increasing integrity and trust to the department: E-SISO will ensure that both parties (the Immigration Department of Malaysia and suspect or “OKT”) are free from any discrimination and lead to justice without prejudice.
Become an innovator: E-SISO will be the first to be implemented in Immigration Department of Malaysia which can be a model for generalization purposes to other public security departments. E-SISO is also improved with a thumbprint system that can ensure the reliability and validity of the processes involved is all secured and free from errors.
Eliminating emotional stress to both parties: This system (E-SISO) can eliminate emotional stress to both parties when it helps to lessening the burden in generating details reports by the officers and the unstable emotions faced by the suspect during the process of arrestment.
Caring about clienteles: Offering security drives higher trust and believing in integrity. When Immigration Department of Malaysia offers security in their process or software as a bonus, the related so called clients will feel that the department are really care about their safety and well-being.
Guaranteeing software interoperability: By adding security, it will help Immigration Department of Malaysia to improve different software systems interoperability. Use of standard security enabled data storage formats and data exchange protocols ensures widest possible interoperability.
Meeting current criterions: In order for Immigration Department of Malaysia to be reliable and up-to-date, a system needs to follow current criterions. Therefore, E-SISO is built in order to meet the requirement of safety and security to officers, suspects and Immigration Department of Malaysia as a whole.
Conclusion
As for exclusivity and viable value factor, E-SISO will be the first to be implemented in Immigration Department of Malaysia which can be a prototypical for generalization purposes to other public security departments. E-SISO is also enhanced with a thumbprint system that can ensure the reliability and validity of the processes involved are all secured and lead to Zero-errors. E-SISO will ensure that both parties (the Immigration Department of Malaysia and PATI) are free from any discrimination and lead to justice without prejudice. E-SISO is also suitable to other public security departments and other related private firms or agencies.
Acknowledgments
This project is under special collaboration between researchers from UNITEN, Sultan Haji Ahmad Shah Campus, Pahang and Immigration Department of Malaysia (Pahang). Special thanks to Dato’ Zamree Hamli, State Director of Immigration Department of Malaysia, Pahang for putting us into the picture and having trust on us to plan and deliver. Special thanks also goes to UNITEN who has been given continuous supports without fail.
References
- Anti-Trafficking in Persons and Anti-Smuggling of Migrants Act 2007(Act 670)
- Cavusoglu H, Mishra B, Raghunathan S. (2004). A model for evaluating IT security investments. Communications of the ACM, 87-92.
- Herath, T., & Rao, H. R. (2009). Protection motivation and deterrence: a framework for security policy compliance in organisations. European Journal of Information Systems, 18(2), 106-125.
- Ifinedo P. (2009). Information technology security management concerns in global financial services institutions: is national culture a differentiator? Information Management & Computer Security, 17(5), 372-387.
- Ifinedo P. (2011). An exploratory study of the relationships between selected contextual factors and information security concerns in global financial services institutions. Journal of Information Security and Privacy. 7(1), 25-49.
- Ifinedo, P. (2012). Understanding information systems security policy compliance: An integration of the theory of planned behavior and the protection motivation theory. Computers & Security, 31(1), 83-95.
- Immigration Department of Malaysia. (2018).
- Lee Y, Larsen KR. (2009). Threat or coping appraisal: determinants of SMB executives’ decision to adopt anti-malware software. European Journal of Information Systems. 18(2), 177-187.
- Padayachee, K. (2012). Taxonomy of compliant information security behavior. Computers & Security, 31(5), 673-680.
- Richardson R. (2010) CSI/FBI Computer Crime and Security Survey. Computer Security Institute. Retrieved from: http://www.gocsi.com/survey on 1/5/2018.
- Rhodes K. (2001). Operations security awareness: the mind has no firewall. Computer Security Journal. 17(3), 1-12.
- Ryan J. (2004). Information security tools and practices: what works? IEEE Transactions on Computers, 53(8), 1060-1063.
- Sasse MA, Brostoff S, Weirich D. (2004). Transforming the weakest link e a human/computer interaction approach to usable and effective security. BT Technology Journal. 19(3), 122-131.
- Sherif, E., Furnell, S., & Clarke, N. (2015). An identification of variables influencing the establishment of information security culture. In International Conference on Human Aspects of Information Security, Privacy, and Trust (pp. 436-448). Springer International Publishing.
- Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information security policies: An exploratory field study. Information & management, 51(2), 217-224.
- Stanton JM, Stam KR, Mastrangelo PM, Jolton JA. (2005). Analysis of end user security behaviors. Computers & Security. 24(2), 124-133.
- Workman M, Bommer HH, Straub D. (2008). Security lapses and the omission of information security measures: a threat control model and empirical test. Computers in Human Behavior, 24(6), 2799-2816.
Copyright information

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
About this article
Publication Date
31 July 2018
Article Doi
eBook ISBN
978-1-80296-043-3
Publisher
Future Academy
Volume
44
Print ISBN (optional)
-
Edition Number
1st Edition
Pages
1-989
Subjects
Business, innovation, sustainability, environment, green business, environmental issues, industry, industrial studies
Cite this article as:
Razak, M. Z. A., Razak, S. F. F. A., Rasli, M. A. M., & Radzuan, N. F. M. (2018). Technology Of Trust: Safely In, Securely Out System (E-Siso). In N. Nadiah Ahmad, N. Raida Abd Rahman, E. Esa, F. Hanim Abdul Rauf, & W. Farhah (Eds.), Interdisciplinary Sustainability Perspectives: Engaging Enviromental, Cultural, Economic and Social Concerns, vol 44. European Proceedings of Social and Behavioural Sciences (pp. 983-989). Future Academy. https://doi.org/10.15405/epsbs.2018.07.02.104

