Abstract
Attendance is a state in which a person is present in the field. An attendance management system is used to administer the attendance-recording process. There have been many systems proposed and implemented to replace manual methods of attendance recording with current trends shifting to NFC, RFID and biometric technology-based approaches. In this research paper, recent approaches implemented in attendance management systems will be explored and comparatively study its authentication aspect. Furthermore, As attendance present a variety of cases, we emphasize on multiple level authentication based on case-based reasoning. In the research, elements are selected from the multiple approaches available and incorporated into the new system framework. A new framework of attendance system was constructed to cater to different situations and the proposed system gains advantage from minimizing administrator user intervention in the system and provide flexibility in cases of attendance authentication. The proposed system presents limitations whereby usage of the system requires Internet connectivity and needs configuration if devices used together with NFC cards are other than smartphone. The results in this paper contributes to a prototype that simulates the functionalities included for detecting authentication from case-based situations. This research paper evaluated the proposed system’s functionalities in comparison to the existing systems. Overall, the evaluation of the prototype in terms of fulfilment of its user requirements has shown that this system has an overall high fulfilment of functionalities achieved.
Keywords: Attendance authenticationcase-basedautomationdata processingmobile
Introduction
The excessive absenteeism by students can drastically hinder the academic achievement of students. Absenteeism has been a common issue and many actions and alternatives have been taken to overcome this problem. Taking attendance is also important as a criterion for any assessment in an academic institution. Therefore, almost every institution or organization has made attendance mandatory as part of their policy. To avoid the possibility of being barred from examination for students, they would need to meet up a certain level of attendance set by their institutions.
The traditional way of taking attendance in most academic institutions are signing their names in the attendance sheet. This method is not only tedious in handling a large number of people and data, but it is also risky in keeping private information safe. For students, a proper attendance recording system can prevent proxy attendance and keep track of attendance performance. Hence, having an automated attendance management system is important for monitoring the attendance progress and preventing such problems mentioned. There are many approaches introduced by various researches over the years. Among those findings, the currently existing systems are largely implemented with NFC, RFID and biometrics technology into the system ( Saparkhojayev, Dauitbayeva, Nurtayev, & Baimenshina, 2014; Arulogun, Olatunbosun, Fakolujo, & Olaniyi, 2013; Ayu & Ahmad, 2014). NFC-based and RFID attendance monitoring systems implement a unique ID using cards or tags as an indicator of the user’s attendance. Biometrics-based systems use physical features from users to indicate attendance.
The three methods possess their own advantages and disadvantages. There is a need to identify elements in which approach may perform better than the others. These systems mostly authenticate attendance confirmation upon validation of fixed criteria set in the system and therefore lack the flexibility. After all, the act of attendance-taking itself is a situation that is affected by various varying factors. The field of this research paper will mainly focus on attendance data processing and management. Data processing is the collection and manipulation of data to produce meaningful information. Data such as attendance records can be used to be analysed in terms of its patterns and present rules and decision-making system to further automate the attendance management system. The objectives of this research are to investigate the existing approaches for attendance management system and to compare the different approaches for attendance data management systems. It is also aimed to identify elements and propose a framework for case-based authentication in attendance data management system.
In this study, the proposed system will be evaluated in comparison to the existing approaches in terms of functionalities. The research approach will be conducted based on a qualitative approach. A research study is performed through relevant researches on the three methods by comparing their method of approach in attendance authentication and their data processing part.
Problem Statement
Attendance management is a system that encompasses different phases ranging from the enrolment process of participants in a session, attendance recording, monitoring to the assessment of the attendance performance. For that reason, the implementation of an intelligent attendance data monitoring system would provide efficient design and framework for the administration of attendance in institutions.
The research topic shall revolve around the management aspect of the attendance data collected and the authentication approach. The main objective of the research study is to identify elements such as authentication of attendance from the existing approaches that have been developed and comparatively discuss them. Each approach will be briefly discussed in the section and comparatively analysed accordingly at the end of the section.
Near Field Communication (NFC)
In an attendance management system, NFC-based technology can consist of three modes: Card Emulation mode, Peer to Peer Mode and Reader/Writer mode ( Saparkhojayev et al., 2014). An NFC-enabled device in card emulation mode replaces a contactless card. Peer to peer mode enables two NFC-enabled devices to share data between them. NFC-enabled devices can read and write to NFC and contactless cards. Before starting, users will need to register and obtain a unique identification. If there are multiple devices, unique identification is needed to distinguish the systems since it is deployed in different places ( Seifedine & Mohamad, 2010). The system can be divided into two units: reader and server unit ( Ichimura & Kamada, 2013). The hardware components for the reader units are NFC-enabled mobile devices/tags whereas the server is the database and application platform. The software required is the client application that will be installed on the NFC devices. The server can generate the unique identification and sends it to the device together with the public-key of the system which is used to encrypt the transmitted data and store them into the database. Then, it can validate the data from the database.
Radio Frequency Identification (RFID)
RFID-based technology implementation in an attendance management system uses a combination of a RFID reader, tags and a mobile platform to detect the attendance of the students ( Arulogun et al., 2013). An RFID reader is used to collect the data scanned from the tag which can be mobile or stationary. The tag is embedded in the student identification card and is encoded with a unique identification. With each scanning scenario, the data encoded in the tag will be read and transmitted to the database. The transmission of the data to the database will be processed and matched to the pre-registered tags in the database ( Sumita, Romin, & Tanvi, 2013). The data obtained from the RFID reader will decide the attendance of the student. The log data from the RFID terminal, its unique serial number along with the student identification data can also be utilised to indicate attendance presence ( Murizah, Hasbullah, Norliza, & Muhammad, 2012). Attendance can be further assessed by the student’s arrival and departure time as logged with each scan of the tag to reader with the time delay taken into consideration.
Biometric
Authenticating the user’s identity using biometric-based technology such as the wireless iris recognition can be applied in taking attendance. In the case of wireless iris recognition, the process involved capturing, extraction, storing and matching the iris to the data in the database ( Ayu & Ahmad, 2014). The flow of the system begins when the user scans their eyes to the eye sensor. The minutiae will be extracted and compared to the ones stored in the database by using a matching algorithm. Whereas, in fingerprint identification system, the fingerprints will be scanned and compared to the pre-registered fingerprint by using ratio of false acceptance rate and false reject rate ( Shoewnu & Idowu, 2012). Overall, the system consists of the physical features data (facial, fingerprints, iris), database and the application system. A scanner is necessary to capture the unique features of the user, algorithms to process the features and a matching process to verify the rate of acceptance. If the system produced a matching result, the attendance is verified.
Discussion
The discussion between the three approaches will be focused on their advantages and disadvantages among the three methods. Table
The three methods all contain certain elements that can be utilised in providing better management of attendance data. There are many elements found in the approaches studied varying with different benefits, weaknesses, and limitations. Most attendance management system functions to only store attendance records but does not fully utilise data processing to understand the strings of patterns the data might possibly present as knowledge. These systems are also rigid in their authentication process. From the above discussion, certain elements are carefully selected. These elements are included as features of the new design framework and will be further discussed and explained in the proposed methodology section in the research paper.
Research Questions
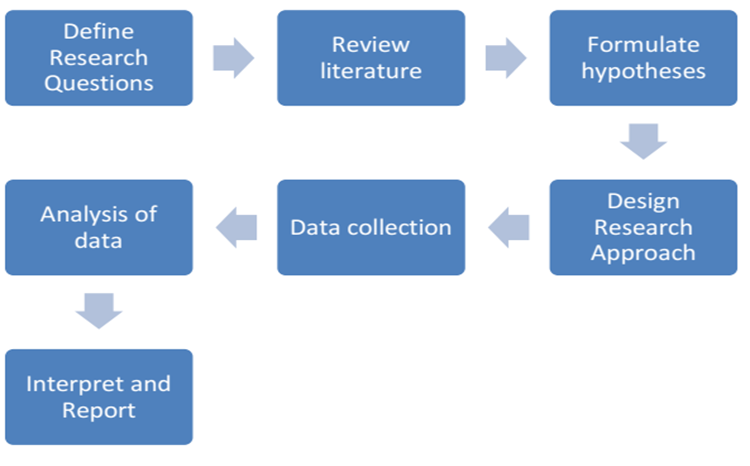
The methodology process will further introduce the approach and implementation steps in the research. The research process as shown in Figure
The research shall be approached using a qualitative approach to investigate the attendance data processing and management in relation to case-based experiences. In the qualitative approach, the Content Analysis Study method is used to examine the patterns and different cases that may be presented from the usage of the attendance management system. Using such approach, knowledge can be derived from the data collected. The process of acquiring knowledge is done through different approaches such as interviews and online resources to collect and identify all the functional and non-functional requirements of the prototype system. After defining the user and system requirements, a prototype of the system will be constructed.
Purpose of the Study
The prototype system will be populated with different data presented in an attendance-taking situation. These data will be analysed and processed according to the different cases. These data will then be categorized into the different case of data to be analysed and test the functionality of the proposed system. In the research study, there is also the need to determine the scope of limitations and delimitations that may affect or constrict the analysis of research data. The limitations in the research investigation are the time constraints and limited data populated as cases into the system. Delimitations in our investigation are focusing only on different elements as identified in existing approaches and emphasis on the data processing in the attendance management system.
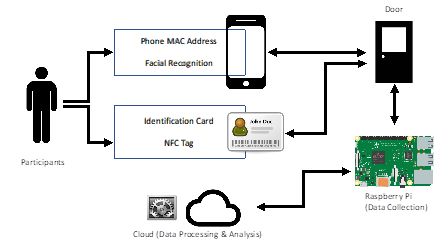
These processes can be divided into three main stages which are Attendance Registration, Attendance Verification (Authentication) and Attendance Performance Assessment. The research will cover the discussion and evaluation of the proposed system in comparison to the existing approaches. The uniqueness of the proposed system lies in the inferencing part constructed as one of the functionalities of the system to determine the authentication process of the system. The proposed system as shown in Figure
Research Methods
The proposed framework comprises several components: server, database, and client application. The client applications specified are smartphones for mobile applications and web-based applications. For web applications, the Apache is suggested as the webserver to deliver the official web pages. The webpage is hosted by WampServer as the webpage can be tested offline first. Hence, the risk of creating problems on live server can be reduced. This server-side scripting language that designed for web development and used as general-purpose programming language has been chosen for the web application. Generally, Firebase is selected as a real-time backend infrastructure primarily for real-time database usage. Firebase is chosen because synchronization of data across devices can be done easily across various applications. There is no need for any server-side coding or RESTful API configuration to show changes in data. Firebase Real-time database is a NoSQL database in which it allows operations to be executed quickly and scalable structures. Hence, users can use their smartphones to connect to the Internet and access the attendance data easily.
Construct of Framework
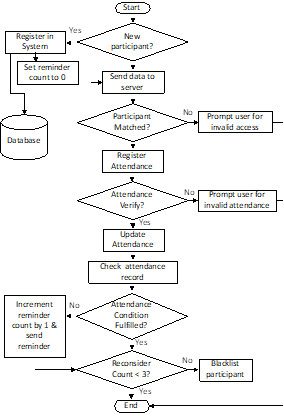
The proposed framework of the system is constructed accordingly to the flow diagram presented in Figure
Multiple identifiers for authentication
Inferencing feature – the combination of inferencing rules and case-based
Alert and notification features
Attendance performance monitoring
Automated attendance assessment
Mobile devices and NFC tags (secondary option) as input
The data will be populated into the prototype and evaluated per fulfilment of requirements. A combination of rules set by the administrator user of the system application and the case-based obtained from the data collected shall be the inferencing part of the proposed system in determining attendance authentication.
Development of the Prototype
Based on the proposed framework, a mobile android and web-based application prototype are constructed. The prototype mainly functions to populate data for testing different situations in attendance process and stimulate the case-based reasoning in the system. There are two parts to the overall framework. All the data processing will be performed in the server application and the data will be retrieved from the client application. Information is stored in Firebase, a cloud-based application that provides services for real-time database stimulation. The data processed into meaningful information will be sent back to the client application – both android and web application in real-time. In attendance authentication phase, the graphical user interface is designed to require minimal human intervention. There is two types of client application, one, mobile application and two, web-application. These two differ in terms of mobility, data visualization, and user experience. Attendance administrators can create participants' accounts and sessions to track attendance records. In terms of user interface, mobile application provides mobility and easy access whereas web-based application provides more variety in data visualization and better user experience in terms of data visibility.
Findings
The data collection process will be carried out by testing the elements included in the proposed framework. The results are obtained by testing different parts of the functionalities in using the prototype application on Android smartphones. The results are then used to measure its fulfilment of user requirements and compared to the existing approaches. The proposed system however only accepts data acquired from smartphone devices with the installed prototype application and NFC tags.
Results and Analysis
The data collected are categorised and then comparatively analysed to discuss functionalities of the proposed system per stages of Attendance Registration, Attendance Verification (Authentication) and Attendance Performance Assessment (see Table
The proposed system includes multiple unique identifiers in the system such as time of arrival, methods of attendance registration and attendance data identifiers such as student identification number. Overall, the proposed system shows fulfilment in providing practical system for attendance recording, interactivity in terms of alert system and automated attendance performance assessment. The new framework is then compared to the existing approaches studied earlier on as shown in Table
It can be observed that the proposed system framework uses a combination of case-based reasoning and inferencing rules. It uses a repository of cases collected from the system. It finds and retrieves a similar case from the repository, and use solution modified from the allowable parameters from the users to solve the authentication. It can add newly adapted situations and solution to the repository as a new case using the proposed framework, the inferencing part records the concrete details of each case without generalizing situations into rules. The system minimises user intervention to avoid personal influence or manipulation of the users. The proposed system looks directly at the data obtained and allowed them to learn and acquire information to fit new situations.
Discussion
The research on the attendance management system has been widely explored in terms of technology and implementation. Much of the attendance management system needs improvement in making “sense” of the data received. As attendance present a variety of cases, we emphasize on multiple level authentication based on case-based reasoning. In the research, elements are selected from the multiple approaches available and incorporated into the new system framework. The proposed system gains advantage from minimizing administrator user intervention in the system and provide flexibility in cases of attendance authentication. The proposed system, however, presents limitations such that the usage of the system requires Internet connectivity and needs configuration if other devices than smartphone and NFC cards are used. The system also prevents the administrator user from adjusting the attendance data. Overall, the evaluation of the prototype in terms of fulfilment of its user requirements has shown that this system has an overall high fulfilment of functionalities achieved.
Conclusion
The result of the framework which differs from the other existing approach is that it allows flexible attendance authentication as authorized by the user administrator. From the different patterns of attendance data collected, the proposed system automated the process of attendance verification and provides an alert system if any of the attendance requirements are violated. Overall, the proposed system in this research paper contains space for further improvement. The user interface and experience of the system plays an important part. It can be further enhanced to provide automated and limited user intervention in the system attracting interface for users. The system is also expected to detect more cases of attendance settings and include better data visualizations in future work.
Acknowledgments
This research is funded under USM RU Grant (PKOMP/8014001) and partly under USM Short Term Grant (PKOMP/6315262) and affiliated with Robotics, Computer Vision & Image Processing (RCVIP) Research Group Lab at School of Computer Sciences, Universiti Sains Malaysia.
References
- Arulogun, O. T., Olatunbosun, A. Fakolujo O. A. and Olaniyi, O.M. (2013). RFID-Based Students Attendance Management System. International Journal of Scientific & Engineering Research, 4(2), 1-9.
- Ayu, M. A., & Ahmad, B. I. (2014). TouchIn: An NFC Supported Attendance System in a University Environment. International Journal of Information and Education Technology, 4(5), 448-453.
- Ichimura, T., & Kamada, S. (2013). Early Discovery of Chronic Non-attenders by using NFC Attendance Management System. In IEEE 6th International Workshop on Computational Intelligence and Applications (pp. 191-196). Hiroshima.
- Murizah, K., Hasbullah, M., Norliza, Z., & Muhammad, K. S. (2012). Web-based Student Attendance System using RFID Technology. In IEEE Control and System Graduate Research Colloquium (pp. 213-218).
- Opoku, S. K. (2013). An Automated Biometric Attendance Management System with Dual Authentication Mechanism Based on Bluetooth and NFC technologies. International Journal of Computer Science and Mobile Computing, 3, 18-25.
- Saparkhojayev, N., Dauitbayeva, A., Nurtayev, A., & Baimenshina, G. (2014). Access Control and Management System Based on the NFC-Technology by the Use of Smart Phones as Keys. Web and Open Access to Learning (ICWOAL).
- Seifedine, K., & Mohamad, S. (2010). Wireless Attendance Management System Based on Iris Recognition Faculty of Science Lebanon, University. Scientific Research and Essays, 5(12), 1428-1435.
- Shoewnu, O., & Idowu, O. A. (2012). Development of Attendance Management System Using Biometrics. Pacific Journal of Science and Technology, 13(1), 301-307.
- Sumita N., Romin R., & Tanvi, S. (2013). RFID Technology Based Attendance Management System. International Journal of Computer Science, 10(1), 1-6.
Copyright information

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
About this article
Publication Date
30 March 2020
Article Doi
eBook ISBN
978-1-80296-080-8
Publisher
European Publisher
Volume
81
Print ISBN (optional)
-
Edition Number
1st Edition
Pages
1-839
Subjects
Business, innovation, sustainability, development studies
Cite this article as:
Sufril, A. M. A., Mohd Nadhir, A. W., Fong, J. W. S., Zawawi, A. S., & Mohd Salleh, N. F. E. (2020). An Intelligent Automated Attendance Data Management System Based On Case Based Authentication. In N. Baba Rahim (Ed.), Multidisciplinary Research as Agent of Change for Industrial Revolution 4.0, vol 81. European Proceedings of Social and Behavioural Sciences (pp. 621-630). European Publisher. https://doi.org/10.15405/epsbs.2020.03.03.72
