Abstract
The study considers the problem of the organization’s personnel security and highlights new methodological foundations in personnel management in terms of personnel security. The emphasis is shifted in understanding the status of a highly skilled employee and the status of an unemployed as a working employee who does not use his labor force. Based on the analysis of domestic and foreign experience in personnel management, the types of personnel threats to the development and existence of the organization are identified. The methods of overcoming them are given. The factors of activating personnel safety threats, some of which are related to the transitional economy, are described in detail. On the basis of scientific research, new patterns are unfolded that take shape in social and labor relations, which become a new methodological basis for modern personnel management. The study suggests the concept monitoring personnel security threats. A tool for the formation of a potential personnel threat in the personnel management process is presented: the better the personnel management system works, the more potential threat poses in the face of highly qualified employees. The emphasis is shifted to managing loyalty of highly qualified personnel, and a new profession – a personnel security manager is introduced. The definition of the concept of a personnel security threat is given, and ways to minimize and / or eliminate these threats are presented.
Keywords: Personnel securitysecurity threathighly skilled personnelunemployedpersonnel managementrecruitment
Introduction
Despite the fact that the Law of the Russian Federation No. 2446-1 “On Security” dated March 5, 1992, defining the state of protection of the vital interests of a person, society and the state from internal and external threats, was adopted quite a long time ago, however, here is a need to consider issues of personnel security within organizations. There are several reasons for this.
Problem Statement
Types of security threats
First of all, we note technical, technological and information components. In the work of modern organizations, almost everywhere in business, they use electronic invoices, stamps, signatures, work in networks, and information technologies. This significantly speeds up transactions, through the creation of a single database, the speed of search and the availability of information is ensured.
However, it also happens that due to technical availability, the risk of data loss increases (Belkovets, 2010; Belyaev, 2009; Bossong, 2014; Haden, 2015; Yankovaya, 2008). In particular, almost always when working in networks one has to use the services of “third” persons - operators, and in the case of information illiteracy - a trusted person. The functioning of organizations shows that the most difficult link in the organization’s security system is its personnel (Kamalova, 2011; Bossong, 2014; Camacho, 2013; Hofmann, 2015). It is the human factor that can have a critical impact on the business success and the very existence of the organization. The possibility of theft, “discharge” of information and its unreliability become clear. Moreover, these hazard cases rarely occur due to malicious, deliberate sabotage on the part of employees of the organization. Most often, information leakage comes from ignorance of еру employee’s behavior.
The study provides a vivid example. The regulations of corporate ethics and the culture of work behavior state that “the workplace should be kept clean upon completion of work”. When working in the office it does not mean that you need to sponge off the working surface of the table. This means that if an employee wants to leave work, or just leave the office, he is obliged to remove all paper media (documents) in a desk or safe, be sure to leave the computer program in which he worked in order to return, re-enter under his password and continue to process the data. In such a situation, a casual visitor who finds himself in an office at the desk of an absent employee, glancing at a table or monitor screen where documents were processed or drafted, cannot voluntarily or involuntarily steal (see, remember ...) corporate information which he has nothing to do with. And this means that the employee himself, precisely following the regulations of the corporate culture, does not create the possibility of information “leaking” to the third side.
Consequently, personnel management services not only need to be literate about the potentially dangerous behavior of employees, but also be able to convey this information reasonably to each employee in the structure of the organization.
In addition to technical, technological and informational components, there are other types of economic security of the organization: financial, legal and environmental (Makhmudova, 2014). And they are all directly related to personnel security threats to the relevant type of work. The poor result of illiterate personnel management, through a hacker or raider seizure, is collapse, merger and absorption of this organization.
Research Questions
Factors of personnel security threats
Almost all negative events are initiated from outside the organization (Bradley, 2018; Ernst & Young, 2017; Serebryakov, 2010). But their active support, and the very possibility of these events, is always ensured by poor personnel security within organizations and poor personnel management (Belyaev, 2018).
On the part of the personnel, other negative events are also possible, creating a threat to the existence or effective development of the organization. Among them: the damage or destruction of the property; the use of the property of the organization for its own purposes, its theft; receiving wages for non-fulfillment of duties; blackmailing with competence (“I am an indispensable employee” or “say thank you that I’m working here for you ...”, “who will come to work for such a salary ...”, etc.). Employers who sell commercial secrets pose a more daring threat, especially if powers are concentrated in the same hands (Vinokurov, 2014; Chumarin, 2003; Yushchenko & Tsareva, 2012; Camacho, 2013; Hofmann, 2015). Threats include any type of disciplinary violation and the creation of an unbearable moral and psychological climate in the team (today there is a special name for this phenomenon - “mobbing” and / or “bossing”).
Purpose of the Study
Minimize or eliminate threats
What can reduce the level of real or potential threats in the organization?
First, it is the correct and effective assessment of personnel loyalty or reliability. Personnel services need to regularly monitor employee satisfaction with the results of labor and the incentive system.
Conducted research allowed measuring the motivational orientation of labor behavior (Makhmudova, 2014). It was noted that in the crisis or transitional (in our case, digital) economy, the perception of labor for all categories of employees is deteriorating. Unemployment, as an external factor influencing the formation of motivational activity, affects not only the emergence of new value orientations for employees, but also the formation of a new attitude to work as a necessity – there is degradation of values, but not needs. This provision becomes a fundamentally new methodological basis for assessing the business activity of an employee and managing his labor behavior. At the same time, employees quite clearly feel their own incompetence and therefore sit tight at work, agreeing to that payment (labor incentive policy), which purely symbolically divides them into functional groups. Thus, the motivational crisis of the personnel was recorded. The reasons for this crisis are due to discrepancy between the goals of the organization and the needs of its employees. There is an inverse relationship between the efficiency of work for the organization and the desire to execute this work on the part of employees.
It should also be noted the tendency to substitute the subject of evaluation by employees, which means not real results of one’s own labor activity, but personal efforts.
At the same time, it is important to note another tendency, which today results in a powerful social phenomenon that changes the very concept of “unemployed status” (Taranin, 2016) - this is a high degree of job dissatisfaction among specialists with a high level of qualification but low status and, accordingly, low wages. For these reasons, they lose their loyalty to their own organization. Continuing to work in it, they are actively looking for a new job, a new workplace, where they can fulfill their potential. In essence, they are “working unemployed”. Why are they unemployed? It happens because these employees do not fulfill their working potential in their own organizations.
Unfortunately, there are a lot of such employees today. The myth that skilled employees can easily and quickly find a job that they dream about, unfortunately, does not work. High-level skill and professionalism can be honed and accumulated, but this takes time, and for an employee it can be years, age. Therefore, status employees, they are also a category of age employees. From the standpoint of personnel management, such employees are listed in risk groups. From the point of view of personnel security, they can be a threat, since they may be most susceptible to recruitment by competing firms.
Until now, security personnel assigned employees in such positions as secretaries, cleaners, system administrators, etc., those who are close to secret commercial information and / or can find it out, as subject to personnel recruiting (Yushchenko & Tsareva, 2012; Haden, 2015). In fact, such employees would have to “play as hired agents, intelligence agents”, which requires special training or additional efforts. Not everyone is capable of such work and will not want to be engaged in “draining” important information, perhaps not from a sense of nobility, but from cowardice or elementary laziness. However, this situation has to be taken into account.
The big potential threat, in this plan, comes from highly skilled, but underestimated employees. They do not have to strain themselves and carry out special “search” measures, they have this information and it is their human capital. And heads of organizations should be aware of this.
There is a saying: keep your friend close and your enemy even closer. This means that personnel services have to regularly identify and work with such potentially dangerous, but extremely useful for the organization, employees.
Such employees need special (comfortable for work) working conditions. In the system of motivation - there should not be a generalized approach to all categories of employees. Each category of persons should have specific goals and different incentives. And, most importantly, employers should not bully into dismissal (Borodin, 1998). They, as it turned out, are waiting for an opportunity to leave this organization! It is much more effective to stimulate them to work actively for the benefit of their own organization, that is, to “secure” them in every way in the organization, through an increase in the level of their loyalty. In addition, they deserve it.
Research Methods
Monitoring system of potential personnel threats
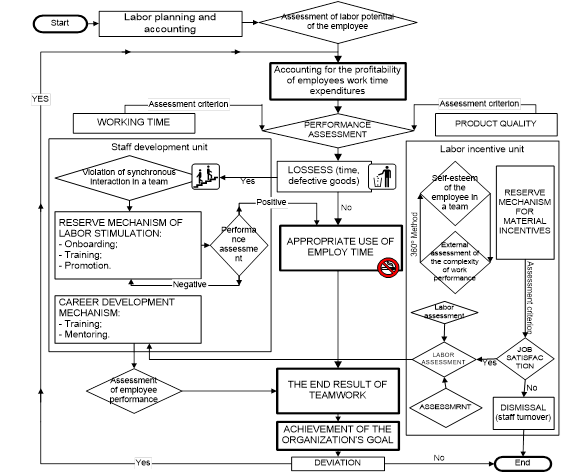
Due to the disclosure of each stage in the employee and team performance in the labor process and the corresponding personnel assessment measures, the study presents a scheme for monitoring potential personnel threats through identifying personnel loyalty (the indicator of “job satisfaction”) (Fig. 01)
This monitoring system includes two blocks - the personnel development block and the labor motivation and incentive block. In accordance with the division of personnel in these blocks, it becomes clear that those employees, who need additional development of professional qualities, do not pose a potential security threat to the organization in their work activities, or this could be random events. It is enough just to eliminate them through the system of onboarding, notification of possible negative consequences due to ignorance and / or misunderstanding. But as soon as they replenish the category of employees who are to be applied the system of motivation and stimulation of work, special attention is given (its degree is determined by the specifics of the organization) to measures that are to be taken to “fix” employees in the organization, and to achieve a high level of their loyalty.
It is easy to see that the more efficiently the personnel management system is and prepares a highly skilled workforce, the greater the potential personnel threat for the organization.
Findings
Summarizing the above, the authors define the notion of a personal security threat (including economic) - this is a real or potentially possible event that contributes to the disruption of organization’s sustainable development or leads to a halt of its activity due to the violation or lack of control over labor regulations by its employees, also personnel management services.
Conclusion
It is necessary to emphasize personnel management, which today are biased and significantly differ from the traditional work with personnel in terms of personnel security.
1. Potential personnel threats can be triggered by the illiterate work of personnel management services.
2. Under new conditions of the digital economy, there are additional personnel threats from the intermediary work, from third parties.
3. The motivation system developed for all employees of the organization is ineffective. Separate categories of employees should be singled out who are applied special incentives in order to increase their loyalty for effective work.
4. Having a highly qualified, but not secured special status in the organization, employees will not be effectively motivated by the threat of dismissal, but by the increase of their loyalty to the organization.
5. A loyalty program or a set of measures should be developed to increase job satisfaction of highly qualified personnel, securing them within their own organization, and not locally.
And finally, for regular monitoring of personnel threats in the organization, it is necessary to introduce a new staffing unit – a personnel security manager. His work will not be replaced by a dozen security personnel, since special training is required in the field of personnel management for making competent management decisions and performing special work on personnel assessment.
References
- Belkovets, V. P. (2010). Personal data: legal regulation. Practical accounting, 3, 28 - 31.
- Belyaev, S. (2008). Guerrilla recruiting as a new method of competition. HR-portal. Retrieved from URL: http://hr-portal.ru/article/partizanskiy-rekruting-kak-novyy-metod-konkurentnoy-borby.
- Belyaev, S. (2009). Aggressive recruiting: Guerrilla recruitment methods. HR-portal. Retrieved from URL: http://hr-portal.ru/article/agressivnyy-rekruting-partizanskie-metody-podbora-personala.
- Borodin, I. (1998). The concept of corporate security. Problems of corporate security. Odessa: Consulting.
- Bossong, R. (2014). EU cooperation on terrorism prevention and violent radicalization: frustrated ambitions or new forms of EU security governance? Cambridge Review of International Affairs, 27 (1), 66-82.
- Bradley, S. (2018). Work is divided into two or a new model of employment / Simon Bradley. - [Electronic resource] - URL: https://www.swissinfo.ch/rus/.
- Camacho, E.T. (2013). The development and interaction of terrorist and fanatic groups. Communications in Nonlinear Science and Numerical Simulation, 18 (11), 3086-3097.
- Chumarin, I. (2003). What is the personnel security of a company? Personnel of the enterprise, 2. [Electronic resource] URL.: http://www.bre.ru/security/20813.html.
- Ernst & Young. (2014). How to prepare for unexpected catastrophic events. HR-portal [Electronic resource] Retrieved from URL: http://www.hr-portal.ru/article/kak-podgotovitsya-k-neozhidannym-katastroficheskim-sobytiyam.
- Haden, J. (2015). Undercover interview. Sly way to talk candidate. HR-portal [Electronic resource] Retrieved from URL: http://hr-portal.ru/blog/intervyu-pod-prikrytiem-hitryy-sposob-razgovorit-kandidata.
- Hofmann, D.C. (2015). Quantifying and qualifying charisma: a theoretical framework for measuring the presence of charismatic authority in terrorist groups. Studies in Conflict and Terrorism, 38 (9), 710-733.
- Kamalova, E. (2011). Processing of personal data in the personnel service. HR-portal [Electronic resource] Retrieved from URL: http://hr-portal.ru/article/obrabotka-personalnyh-dannyh-v-kadrovoy-sluzhbe
- Makhmudova, I.N. (2014). Appraisal personnel-technologies: management practice [Monograph]. Samara: Samara University Publishing House
- Serebryakov, A.V. (2010). Formation of the category of “promoting terrorist activities” in the norms of international criminal law. Society and Law, 3, 140-143.
- Taranin, A. (2016). More and more factories transfer employees to part-time employment. [Electronic resource] Retrieved from URL: Https://www.vedomosti.ru/management/articles/2016/03/02/632119-vse-bolshe-zavodov-perevodyat-rabotnikov-nepolnuyu-zanyatost. Reference date: 04.10.2017.
- Vinokurov, M. А. (2014). Ensuring personnel security of the organization: the criminological aspect. Criminological journal of the Baikal State University of Economics and Law, 4, 54-64.
- Yankovaya, V.F. (2008). Regulations on the protection of personal data of employees. Novato, California: Professional Publishing, LLC
- Yushchenko, D., & Tsareva, N. (2012). Recruitment in business. Recruiting for personnel officers, 12. [Electronic resource] Retrieved from URL: http://hr-portal.ru/article/verbovka-v-biznese. Reference date: 29.08. 2017.
Copyright information

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
About this article
Publication Date
20 March 2019
Article Doi
eBook ISBN
978-1-80296-056-3
Publisher
Future Academy
Volume
57
Print ISBN (optional)
-
Edition Number
1st Edition
Pages
1-1887
Subjects
Business, business ethics, social responsibility, innovation, ethical issues, scientific developments, technological developments
Cite this article as:
Makhmudova, I., Ilyukhina, L., & Bogatyreva, I. (2019). Personnel Safety In The System Of Economic Security And Personnel Management. In V. Mantulenko (Ed.), Global Challenges and Prospects of the Modern Economic Development, vol 57. European Proceedings of Social and Behavioural Sciences (pp. 1859-1865). Future Academy. https://doi.org/10.15405/epsbs.2019.03.189

