Abstract
According to the Business Dictionary (
Keywords: Organizational risksrisk management methods
Introduction
As per the International Standards Organization (ISO), risk relates to the uncertainty arising from
any known or unknown sources. In order to manage the risk, it is useful to understand how the
organization/ the system works. A system is said to be a set of tangible and intangible components
working together to achieve a common goal (Bright Hub Inc, 2017).According to (E.N.I.S.A Technical
Department, 2006), the management of risks consists of:
• Definition of the scope and framework for the management of risks;
• Assessment of the security risks;
• Treatment of security risks;
• Communication of risks ;
• Monitoring and reviewing;
• Acceptance of risks (the decision of accepting a risk by the top management).
There are a lot of methods / methodologies to manage the risk (all type of risks) in an organization,
an analysis of these can be found in the chapters listed below.
Typically, risk management plans have the following objectives:
1.To eliminate negative situations/events.
2.To reduce risks to an acceptable level, if these risks cannot be removed. This implies that there will
be a risk level the company can accept, making sure that optimal controls are in place to keep risks
within an acceptable range - based on (The Institute of Internal Auditors, 2017).
3.To transfer the risks from a company to another one – for example using a third-party
provider/vendor to install network equipment so that the provider/vendor is made responsible for the
installation's failure or success; or to transfer risks by means of insurance – for example the insuring
company assets for destruction or theft, for example fire damage or hurricane - based on (The
Institute of Internal Auditors, 2017).
Problem Statement
There are a lot of general tools and methodologies used for risk management such as - based on
(Clarizen Inc., 2017):
�Brainstorming;
�Delphi technique;
�Interviewing;
�Checklist analysis;
�Risk probability and impact assessment;
�Probability and impact matrix / Risk categorization;
�Quantitative risk analysis & modelling techniques;
�Expected Monetary Value analysis (EMV) ;
�Cost risk analysis;
But, in addition to these general methodologies, there are methods used for risk management with
special characteristics which refer to:
compatibility with the software tools (tools which support the method)
consultancy support,
target organization,
geographical spread,
certification possibility.
It is useful to have a descriptive view of these methods used in the risk management process in an
organization. In the next sections, a comparative analysis of the risk management methods is presented,
with the mention that this analysis is based on some certain criterions.
Research Questions
1.Which are the most commonly used methods for risk management in an organization?
2.Which are the main characteristics of each method used for risk management?
3.Which is the most suitable method of risk management taking into consideration the following
criterions: compatibility with tools, consultancy support, skills needed to introduce/use/
maintain, target organization, geographical spread, certification possibility?
Purpose of the Study
The research is an exploratory study, having as the main scope, a comparative presentation of
various methods used for risk management in an organization.
The main objectives of the research are listed down below:
To present in a descriptive manner some methods used for risk management: Ebios, It-Grundschutz, Marion, Mehari, ISO 27001
To undertake a comparative study regarding some risk management methods based on some criterions, such as: compatibility with tools, consultancy support, skills needed to introduce/use/maintain, target organization, geographical spread, certification possibility etc. This comparative presentation represents the main objective of the paper.
To develop some conclusions (useful for organization’s management) based on the research findings on a topic that is both timely and important, that is risk management in an organization.
Research Methods
The research methods and tools used in this paper consist of:
�Bibliographical research;
�Comparative analysis;
�Exploratory study;
�Descriptive approach;
Every method has been analysed using a set of criterions: compatibility with tools, consultancy
support, skills needed to introduce/use/maintain, target organization, geographical spread, certification
possibility etc.
The descriptive approach represents the presentation of the main characteristics of each method.
Findings
6.1 The methods – a descriptive approach
It is useful to have a descriptive view of the above mentioned methods used in risk management
process. This non-exhaustive study presents, based on some bibliographic sources (E.N.I.S.A, 2006) and
the authors’ experience, five methods.
6.1.1. Ebios - Expression des Besoins et Identification des Objectifs de Sécurité is a widespread
method (a set of guides supports the software tool) for risk management. It originates from France,
but now the method is managed by a club of experts from different countries. The method helps
managers to reach a global and coherent vision, plus it is useful when it comes to supporting the
process of decision making in an organization regarding its security policies, business continuity
planning etc. EBIOS consists of 5 stages (Ţigănoaia, 2012):
Stage 1: Context analysis, global business process dependency on the information system:
perimeter definition, decomposition into information flows, etc;
Stage 2 and 3: Threats and security necessities analysis;
Stage 4 and 5: Risk analysis (it also includes the residual risks) and the proposals for increased
security measures.
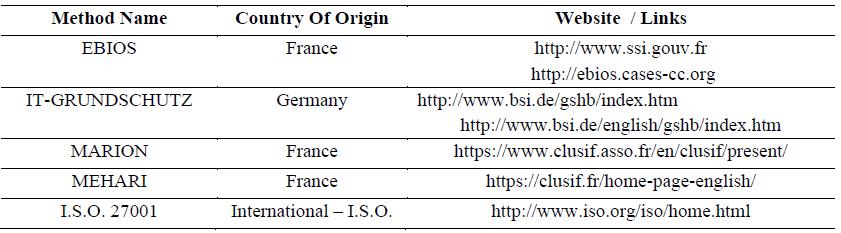
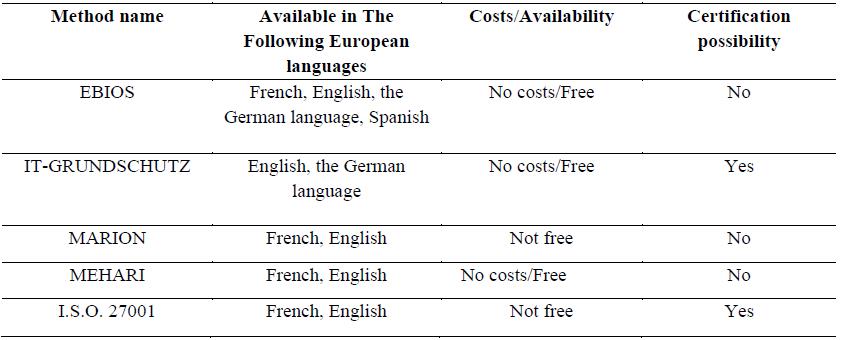
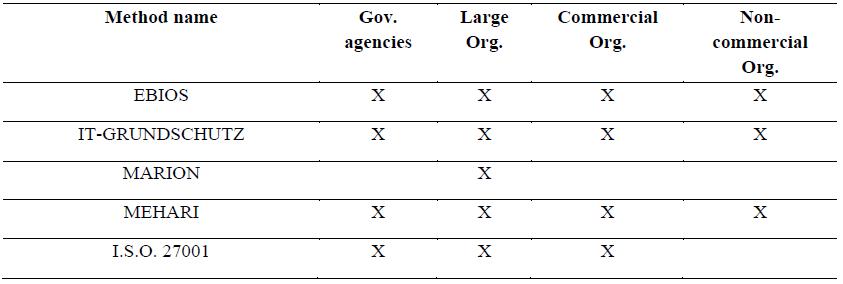
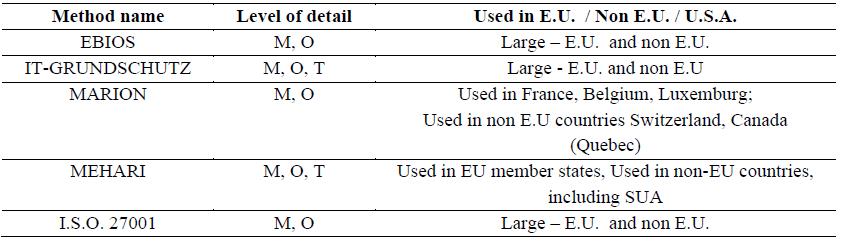
More information about the method in Tables 1-6.
6.1.2. It-Grundschutz – In order to implement an ISMS – Information Security Management
System
in an organization, IT- GRUNDSCHUTZ provides a method. The method consists of:
generic recommendations regarding IT security;
technical recommendations to obtain the optimal IT level for a specific field.
The IT security process suggested by IT-Grundschutz consists of the following steps (ENISA ITGrundschutz,
2017):
Initialization of the process:
Definition of IT security goals and business environment;
Establishment of an organizational structure for IT security;
Provision of the necessary resources;
Creation of the IT Security Concept:
IT-Structure Analysis;
Assessment of protection requirements;
Modelling;
IT Security Checks;
Supplementary Security Analysis;
Implementation planning and fulfilment;
Maintenance, monitoring and improvement of the process;
IT-Grundschutz Certification (optional).
IT-Grundschutz:
provides a framework for IT security management;
lists the relevant threats and required countermeasures - these elements can be adapted according
to the needs of the organization.
More information about this method can be found in Tables from 1 to 6.
Methodology of audit for estimating the level of IT security risks of an organization (for which have
been used questionnaires);
For the estimation of the security level there are used 27 indicators (each of them assigns a grade
between 0 and 4) and it’s categorized in 6 main domains;
Level 3 is the level which is considered as “correct” for an organization;
The objectives of MARION are:
- to estimate the security level of a company in comparison with level 3 – level considered as “correct”;
- to compare the security level of the organization with other companies which have answered to the same
questionnaire;
Finally, a more detailed risk analysis is needed in order to identify threats and vulnerabilities of a
company.
Note: The CLUSIF does not sponsor this method anymore, as MARION has been replaced by MEHARI.
However, MARION is still used by various companies (E.N.I.S.A. Marion, 2017). More information
about this method can be found in Tables from 1 to 6.
provides a complete risk management model compliant to ISO 27005 requirements;
includes the classification of assets, the likelihood of the threats and it also measures the
vulnerabilities through audit;
analyzes a generic list of risk situations and provides seriousness levels for each scenario;
bases its analysis on formulas and parameters;
allows an optimal selection of corrective actions;
can be considered also as an RA/RM tool by the automatic use of formulas.
More information about this method can be found in Tables from 1 to 6.
comparison of an Information Security Management System through a series of controls. This standard
does not cover risk analysis or certification of the risk management (E.N.I.S.A. Inventory of Risk
Management, 2017). ISO/IEC 27001 is the best-known standard in the family providing requirements for
an information security management system (ISMS). Like any other ISO management system standards,
certification to ISO/IEC 27001 is possible but not mandatory. Some organizations choose to implement
the standard in order to benefit from the best practice it contains while others decide they also want to get
certified to reassure customers and clients that its recommendations have been followed (
More information about the method can be found in Tables from 1 to 6.
6.2. The methods - A Comparative Approach
It is useful to have a comparative view of these methods based on some common criterions. Using
a template, each method is analysed, the data is from (E.N.I.S.A Technical Department, 2006) and
(E.N.I.S.A. Inventory of Risk Management, 2017). The comparison can be found below, tables from 1 to
6.
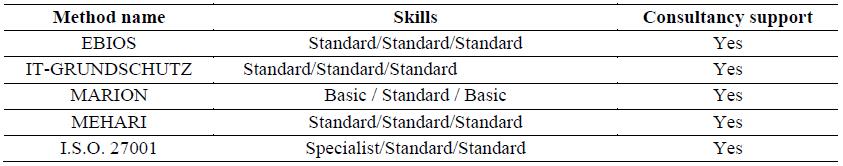
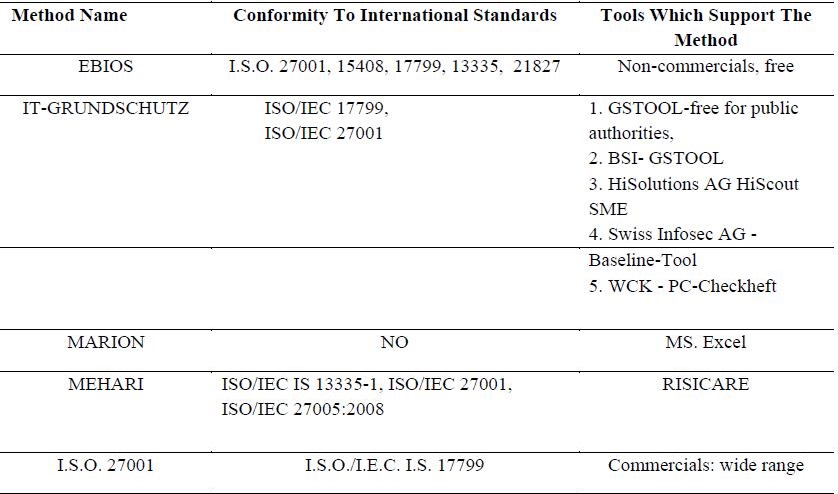
Conclusion
It is useful to have a look at the methods used for identification, evaluation and treatment of risks.
The paper presents, in a comparative manner, various methods used for risk management in an
organization. The results can be used by both the academic and industrial sector. Industry demands more
than just “talking about risks”, especially hazardous ones, where very large private investments are at
stake and critical consequences are lurking (Oboni, 2013).
Instead of a conclusion, as a result of studying the international literature, the risk assessment
process encompasses the following steps (Oboni, 2013):
Defining the context and boundaries of the system;
Describing the system in terms of elements and links;
Identifying the hazards and fundamental failure modes;
Evaluation of the probability of hazards and fundamental and compound failure
modes occurring;
Evaluation of potential targets and costs of failure;
Determination of tolerable versus intolerable risks;
Present Risk and Decision Making based on risk prioritization.
A risk can be acceptable for an organization, while the same risk can be unacceptable for another
one. As future opened issues, the concepts of risk tolerance and interoperability of methods can be
analysed.
Acknowledgments
This work has been funded by University Politehnica of Bucharest, through the “Excellence
Research Grants” Program, UPB – GEX. Identifier: UPB–EXCELENȚĂ–2016, Contract number
11/30.09.2016.
References
- Bright Hub Inc. (2017). The Basics of Risk Management, Retrieved from http://www.brighthubpm.com/risk-management/71742-the-basics-of-risk-management/
- Clarizen Inc. (2017). Risk Management - Useful Tools and Techniques,. Retrieved from
- https://success.clarizen.com/hc/en-us/community/posts/203996208-Risk-Management-Useful-Tools-and-
- Techniques
- E.N.I.S.A (Technical Department). (2006). Risk Management: Implementation principles and Inventories for Risk Management/Risk Assessment methods and tools, Retrieved from http://www.enisa.europa.eu E.N.I.S.A. (2017). Inventory of Risk Management / Risk Assessment Methods, Retrieved fromhttps://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/riskmanagement-inventory/rm-ra-methods E.N.I.S.A. (2017). IT-Grundschutz, Retrieved from https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-ramethods/m_it_grundschutz.html E.N.I.S.A. (2017). Marion, Retrieved from https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-ramethods/m_marion.html E.N.I.S.A. (2017). Mehari, Retrieved from https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/rm-ramethods/m_mehari.html E.N.I.S.A. (2017).Inventory of Risk Management / Risk Assessment Methods and Tools, Retrieved fromhttps://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/riskmanagement-inventory Oboni, F., Oboni, C., (2013). What You Need to Know About Risk Management Methods, Riskope International.
- Sennewald, C. A., Baillie, C., (2016). Chapter 21 – International Security Standards, Effective Security Management Sixth Edition, (pp. 205–212).
- The Institute of Internal Auditors. (2017. )Understanding the Risk Management Process,Retrieved from https://iaonline.theiia.org/understanding-the-risk-management-process Ţigănoaia,B. (2012). “Comparative study regarding the methods used for security risk management”, Nic. Bal. La. For. Acad. Sci. Bull., XVII, No. 2 (34), 149.
- Web Finance Inc. (2017). Business Dictionary, Retrieved from http://www.businessdictionary.com/definition/risk-management.html
Copyright information

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
About this article
Publication Date
06 July 2017
Article Doi
eBook ISBN
978-1-80296-024-2
Publisher
Future Academy
Volume
25
Print ISBN (optional)
-
Edition Number
1st Edition
Pages
1-74
Subjects
Education, design learning, educational technology
Cite this article as:
Tiganoaia, B., & Cercel, C. (2017). Methods Used In The Risk Management Process – A Comparative Approach. In Z. Bekirogullari, M. Y. Minas, & R. X. Thambusamy (Eds.), Living the Future: Technology, Engineering, Education & Computer, vol 25. European Proceedings of Social and Behavioural Sciences (pp. 48-56). Future Academy. https://doi.org/10.15405/epsbs.2017.07.5

