Abstract
The article describes the organizational methods of the process of introduction of risk management in IT-projects. These organizational methods make it possible to eliminate the contradiction that arises among the requirements addressed to the risk management executives of IT-organizations, IT-project managers, practitioners. The essence of the contradiction lies in the fact that risk management should provide maximum convergence of the actual and planned results (a variation of less than 5%), but it should not change the existing model of management in IT-projects (Waterfall, Agile, etc.). We shall note that in 2014, according to The Standish Group International, a variation between actual and planned results in IT-projects was 89%. The article also presents the results of experimental testing of organizational methods of the process of introduction of risk management in an IT-project, according to which the variation between actual and planned results was 4.5%. The results of the study will be of interest to project managers, project team members and also all who are engaged in project activities.
Keywords: Riskrisk managementIT-project
Introduction
Projects implemented in the field of information technology (IT-projects) are a complex of scientific, engineering and technological disciplines, requiring extensive training, high investment costs, high technology equipment, and experienced professionals. The complexity of the IT-project implementation creates risk zones, which leads to decrease in number of successful IT projects (maximum convergence of actual and planned results) (The CHAOS Manifesto, 2013).
An IT organization is influenced by a variety of factors generated by both external and internal environment (Nikylina et al., 2009). For example, O.K.D. Lee and D.V. Baby confirm this fact in their work with the results of conducted researches. The scholars come to a conclusion that factors of external (natural and operating environment) and internal (people, technologies) environments are the main sources of uncertainty, which increase the probability of financial and other losses (Lee, & Baby, 2013). In relation to organizations, it means a probability of a situation suddenly occurring in endogenous and exogenous environment and affecting planning, investments, production, and/or any other business process (De Bakker et al., 2010). For example, exogenous environment negative risks for an IT-organization can be threats related to poorly elaborated schedules, incorrectly planned budget, lack of professional staff, Cassandra complex in communications between stakeholders, etc. (Streles, 2006). Threats related to fluctuation of exchange markets, changes in tax legislation, political and economic relations between countries are referred to as endogenous environment negative risks (Petukhov, & Nikolaenko, 2014).
We shall note that this article uses the definition of risk as a probable event which may have both negative and positive impact on the successful completion of an IT-project (Nikolaenko, 2015).
The analysis of scientific works on risk management has shown that scholars mainly take into account common risks, which do not reflect the peculiarities and specificities of the information technology sphere. Moreover, most works cast the risk in a negative light. In this regard, many practitioners, heads of IT-organizations and IT-project managers refuse to use risk management, because current methods of risk management and its implementation substantially complicate IT-projects management.
In connection with this, the purpose of the article is to resolve contradictions which may occur among requirements imposed on risk management in IT-projects, namely:
introduction of risk management should not change existing and established IT-project management, i.e. project management should remain unchanged (Waterfall, Agile, etc.);
introduction of risk management should contribute to minimize variation between actual and planned results.
We shall note that, according to the statistical data published in The Standish Group International reports in 2014, the average variation in the planned budgets, timescales and quality was 89% (The CHAOS Manifesto, 2014).
This contradiction was resolved through solution of the following tasks:
Analysis of methods used to complete basic processes of risk management;
Elaboration of organizational methods for introduction of risk management into IT-projects;
Experimental approval of the elaborated organizational methods for introduction of risk management into IT-projects. The introduction results showcased a 4,5% variation between actual and planned results, i.e. the resource overrun turned out to be 19 times less in comparison with the 89% average variation.
Methods
We shall examine solution of every task in more depth.
Elaboration of organizational methods for introduction of risk management into IT-projects requires creation of a complex approach and effective risk management which would help an IT-project manager to identify, analyze, control risk events and respond to them without delay. Thus, the solution of set tasks requires analysis and adaptation of heuristic methods (methods used to find the optimal solution) for every process of risk management (Krakovetskaya, & Nikolaenko, 2013).
Identification of IT-project risks
We suggest carrying out the following actions in order to identify risks in IT-projects:
To analyze project documentation in order to identify risks concerning the planned results, timescale, budget, specified requirements, etc., including the risks which previously occurred in other IT projects;
To use the method of Process Decision Program Chart (PDPC) (Efimov, 2011);
To use questionnaires (Daibova, & Nikolaenko, 2015);
To use the brainstorming method, intensifying it with the game «Speed Boat». It is recommended that a full project team, including an IT-project manager and invited experts, participate in brainstorming (Nikolaenko, 2014);
To use the method of SWOT-analysis (Strengths, Weaknesses, Opportunities, Threats). The use of this method enables us to simultaneously identify both negative and positive risk events;
To conduct an expert interview. The interview is to be conducted with experts who have experience of implementation of similar IT-projects.
IT-project risk analysis
We suggest conducting the analysis using qualitative (expert) methods for assessing the probability of risk events occurrence and their impact due to the following factors:
limited time for the planning stage in real production environment (quantitative methods will require significant labor costs, time resources and respective knowledge, skills, and experience at the hand of the IT-project manager);
use of the KISS technique (Keep it Short and Simple). KISS is a way of IT-projects design and development which considers simple wording as the major value of project implementation (quantitative methods for risk assessment require substantial process formalization);
use of basic approaches of agile implementation listed in Agile Manifesto (Manifesto for Agile Software Development). Agile sets priorities according to which people and their interactions are more important than processes and tools. Consequently, use of qualitative methods in all risk management processes promotes interaction, trust, and communication among the project team members;
according to the definition of the project, every IT-project is unique, which limits the possibility of using information data from other IT-projects (Gaga, & Nikolaenko, 2013);
it is not rational to use quantitative methods in small projects (with period of implementation less than two months) due to complexity and labor intensity of these methods;
iterative implementation of an IT-project requires quick and flexible implementation of all basic risk management processes.
In connection therewith, it is suggested to use the following heuristic methods in order to assess the damage in case of negative risk occurrence or a possible positive effect should positive risks eventuate:
Bow-tie: the first stage reinforced by the 5 Whys method (Lewis, Smith, 2010). We shall note that the Bow-tie method combines the features of the Event Tree Analysis (ETA) and the Fault Tree Analysis (FTA) (ISO/IEC 31010:2009);
Ishikawa Fishbone Diagram (Ishikawa, 1986);
Interviewing.
Risk response
The author suggests elaborating creative activities for risk response with the help of:
Bow-tie method – the second stage;
Walt Disney method;
Method of Six Thinking Hats by Edward de Bono (1985);
Brainstorming method;
Delphi Technique.
It is suggested to use a variety of heuristic methods for different categories of negative (Tigers, Alligators, Puppies and Kittens) and positive (Elephants, Dolphins, Dogs and Rabbits) risks. For example, it is suggested to use methods which identify the cause of the risk, its possible consequences and relations to other risks for the risks defined as critical. Such detailed analysis of the critical risks enables experts to assess these risks comprehensively and to determine the possible probability and impact more accurately.
We shall note that an IT-project manager does not have sufficient resources to provide quality management of all identified negative and positive risks in a real work situation. Thus, prioritizing different risk categories enables an IT-project manager and a project team to focus limited resources on management of the most critical risks. For example, measures of Plan A, triggers and measures of Plan B should be primarily elaborated for the negative risks, categorized as critical (Tigers). Then the unpredictable (Alligators) and common (Puppies) risks are analyzed. Risks considered as low-level (Kittens) have the lowest priority.
In connection therewith, in order to manage high priority risks (Tigers & Dolphins), it is suggested to elaborate:
Risk Response Plan, or Plan A, a plan of proactive measures in order to eliminate, mitigate, transfer, and adapt the negative risks, and to use, reinforce, divide, and to accept the positive risks;
triggers, indicators of risk occurrence, i.e. characteristics which make the designated person responsible for the risk understand that proactive «Plan A» measures have not given the expected result;
A Bugout Plan, or the Plan B, a plan of measures which involves activities in case of occurrence of a risk event.
Elaboration of creative measures of «Plan A» and triggers are enough for the risks labeled as alligators, puppies, and dogs. Risks identified as kittens, elephants, and rabbits can be disregarded.
Subsequently, we will examine an adaptation of heuristic methods for elaboration of creative response measures for risks of each category in a greater detail.
Critical methods (Tigers). As critical risks have a significant impact on successful completion of an IT-project, occurrence of just one tiger risk stops the project. In connection with this, it is suggested to elaborate creative «Plan A» actions, «Plan B» and triggers using:
Bow-tie method – the second stage;
Walt Disney method;
Method of Six Thinking Hats by Edward de Bono;
Delphi technique, intensified by interviewing.
Risk monitoring and control in IT projects
The best measure that ensures control over triggers of identified risk events is distribution of responsibilities among IT-project team members, i.e. «personal responsibility for the risk». Such delegation of control tasks can be explained by the fact that the triggers of risk events are not universal and can be pointed out only by certain specialists. For example, it is a software code designer who should control the trigger «during testing a software code bug was detected» for the risk «a functionality planned for iteration will not end on time», because he can point out evidences of a risk event occurrence earlier than an IT-project manager does.
Moreover, we shall note that the process of monitoring and control can be explained by the life cycle model chosen for IT-project development (Lopez, & Salmeron, 2012). For example, in case of the iterative life cycle model, we suggest bringing up the following questions for discussion in a project team:
All functionalities and tasks, planned for iteration, are completed. If not, what are the reasons?
Are there any new identified risk events, which may have an impact on successful completion of the IT-project? If yes, there is a need to:
estimate probability and impact of the identified risk;
disregard the risk, if it is a low-level risk;
develop response measures, if the risk is critical, unpredictable or common.
Have triggers of the identified risk events been noted? If yes, then the Plan B measures are accepted.
Results
According to the elaborated organizational methods, we conducted an experimental testing of introduction of risk management into a small IT-project (implementation period is less than 2 months).
Accompanying project documentation was studied and an interview with each project team member was conducted at the stage of identification. As a result, a sub-register of risk events «Risk identification» was created with a description of 54 negative and 14 positive risk events.
The project team members made an expert assessment of negative and positive risk events using methods of risk analysis and Harrington’s verbal and numeric scale.
Expert assessment of probability of occurrence and impact of risk events showed that 17 (31,4%) risks are critical, 35 (64,8%), are unpredictable, 1 (1,9%) is common, and 1 (1,9%) is low-level of the total amount of 54 (100%) negative risks. Talking about 14 (100%) positive risks, 10 of them (71,4%) are constructive, and 4 (28,6%) are unpredictable. (Figure
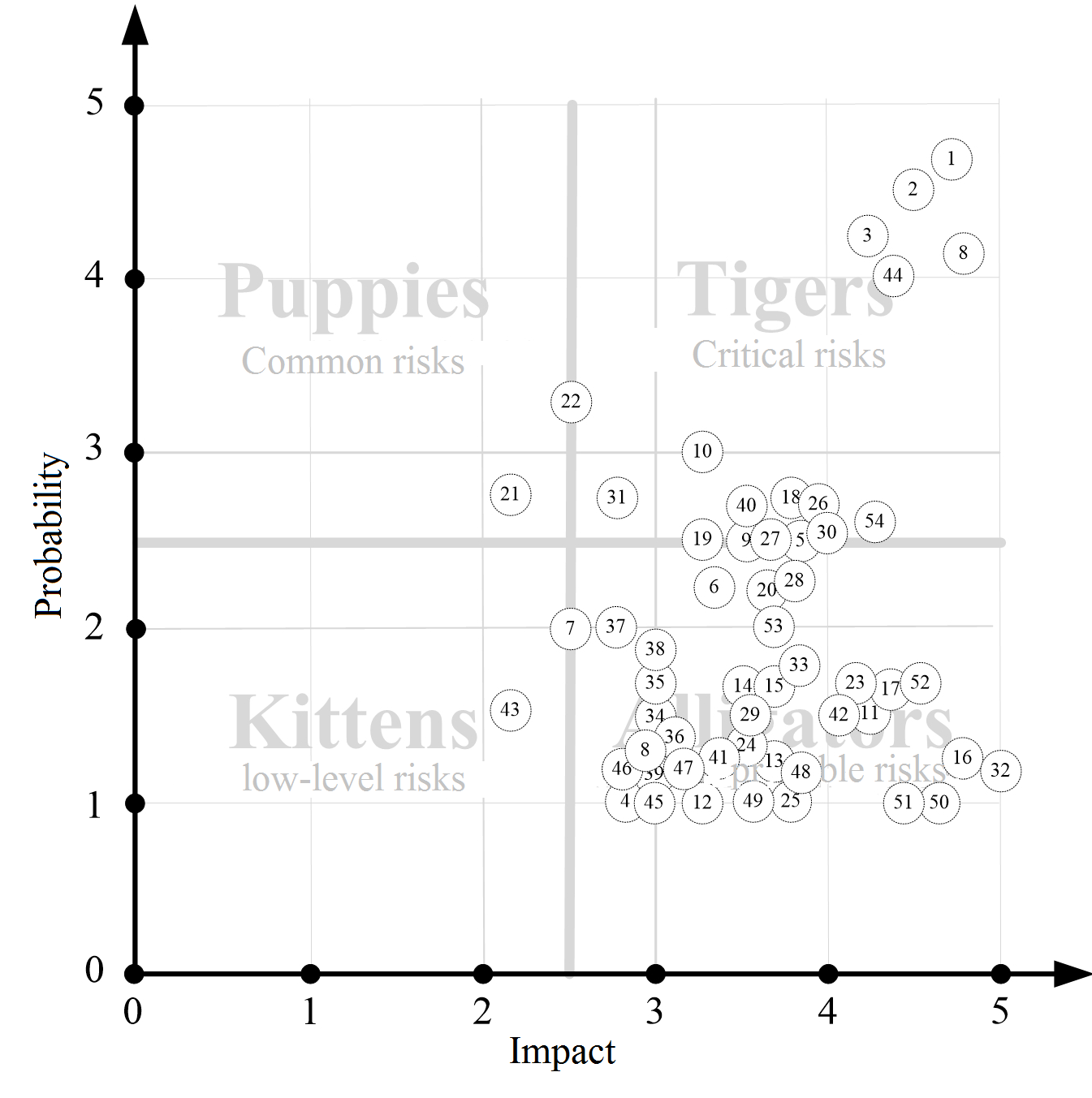
As more than 70% of positive risks were considered as elephants, i.e. risks which can occur in the project regardless the efforts of the project team, the project manager decided not to develop measures which would increase the probability of occurrence of four risks identified as dolphins. Thus, all the resources were focused on management of critical (Tigers) and unpredictable (Alligators) negative risks.
We shall note that the project team members developed measures of Plan A, triggers and measures of Plan B for 27 identified negative risks before the implementation of the IT-project (Figure
First of all, the project team members focused on the risks defined as tigers. But proactive response measures were not developed for each risk. For example, the risks «Project members can get ill» and «Project members can face force majeure» were defined as risk events that cannot be managed. In connection with this, proactive measures were developed and taken in case of only 15 of 17 tigers.
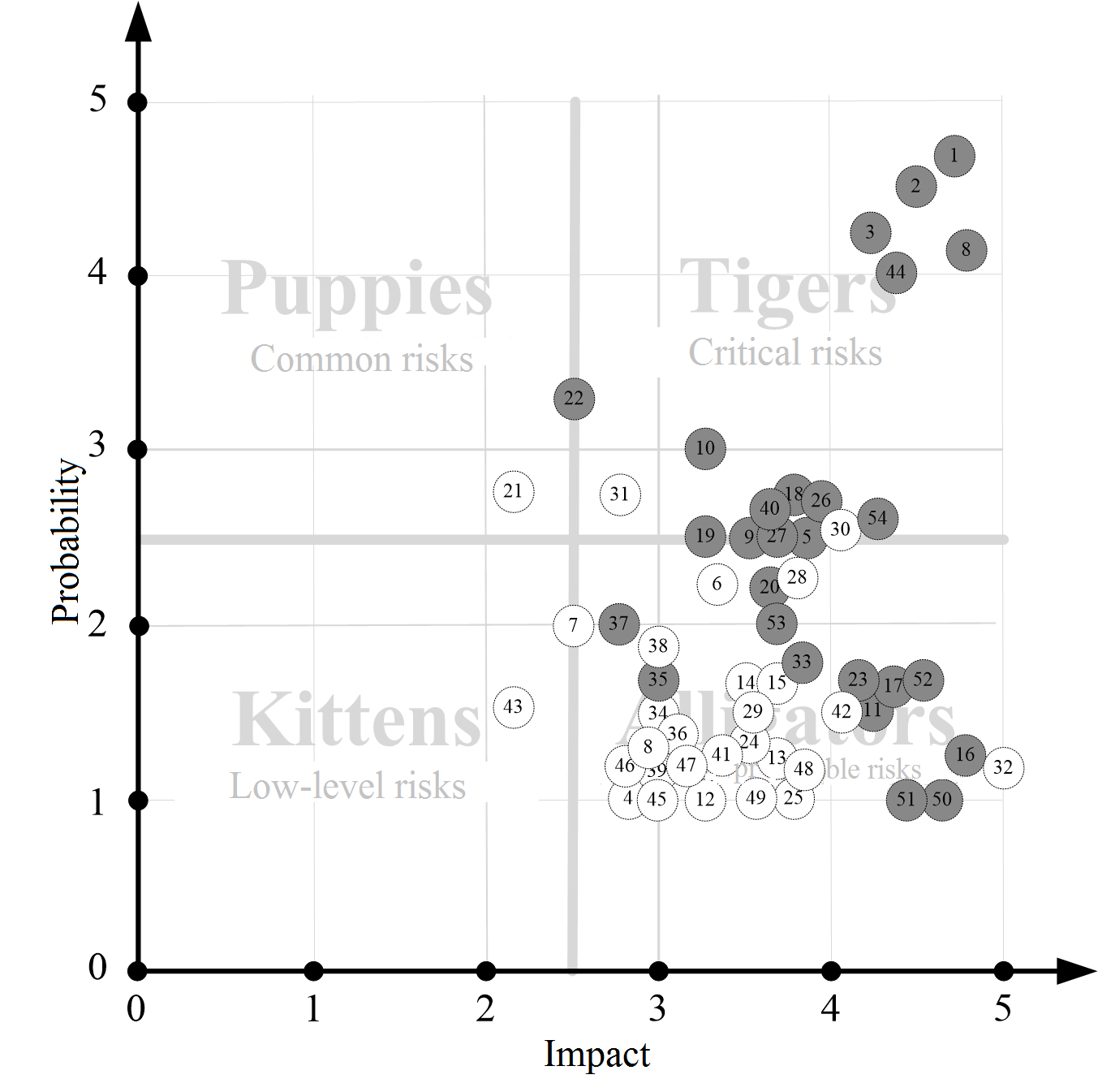
Then the project team members developed creative response measures for 11 of 35 risks are defined as alligators. The development of Plan A and Plan B for alligators had been conducted till the limit cost of resources, allocated for risk management, was reached.
After the completion of the works on the project, the duration of implementation of the IT-project turned out to be 69 days, which is 3 days more than stated in the accepted baseline plan. This variation can be explained by occurrence of two identified risks: «The results of development were not reviewed by the Product Owner on time» and «Design of the web page changed due to re-branding of the organization of the Product Owner». These risks were transferred to the Product Owner, because a time delay, which influenced the project duration, was Product Owner’s fault.
Conclusion
According to the scheduled plan, the duration of the IT-project was 66 office days. The actual duration of the IT-project turned out to be 69 office days. Thus, the variation of the actual and the planned is 4,5%. In comparison with the statistical data, presented by The Standish Group International in 2014, the variation is 19 times less (89% and 4,5% respectively).
An applied research task concerning the introduction of risk management in IT-projects was solved on the basis of the conducted research and experimental testing. This solution eliminated a contradiction between requirements specified for risk management in IT-projects, namely:
introduction of risk management did not change the current IT-project management (Waterfall);
according to organizational methods, introduction of risk management led to a 4,5% variation between actual and planned results.
References
- Daibova, K.E., Nikolaenko, V.S. (2015). Development of tools for the rapid identification of risks in IT-projects. Resource-efficient technologies – energy and enthusiasm of young people: proceedings of the VI all-Russian conference. 254-257.
- De Bakker, K., Boonstra, A., Wortmann, H. (2010). Does Risk Management Contribute to IT Project Success? A Mete-Analysis of Empirical Evidence. International of Project Management, 1-23.
- De Bono, E. (1985) Six thinking hats. Little. Brown Book Group Limited, 207.
- Efimov, V.V. (2011) Collection of methods to search for new ideas and solutions quality management. UlSTU, 194.
- Gaga, V.A., & Nikolaenko, V.S. (2013) The establishment of a project management system in the organization with the use of heuristic methods. Vestnik of Tomsk State University, 374, 137-140.
- Ishikawa, K. (1986) Guide to quality control. Asian Productivity Organization, 226.
- ISO/IEC 31010:2009, Risk management – Risk assessment techniques.
- Krakovetskaya, I.V., Nikolaenko, V.S. (2013) Activate the creative potential of staff using heuristic methods during site development. Journal of Creative Economy, 10(82), 37-43.
- Lee, O.K.D., Baby, D.V. (2013). Managing dynamic risks in global IT projects: agile risk-management using the principles of service-oriented architecture. International Journal of Information Technology & Decision Making, 6, 1121-1150.
- Lewis, S., Smith, K. (2010). Lessons Learned from Real World Application of the Bow-tie Method. 6th Global Congress on Process Safety, 1-20.
- Lopez, C., Salmeron, J.L. (2012). Monitoring software maintenance project risks. Procedia Technology, 5, 363-368.
- Manifesto for Agile Software Development. http://agilemanifesto.org
- Nikolaenko, V.S. (2014). Ways to enhance the creative potential of the project team, using heuristic methods. Journal of Creative Economy, 01(85). 18-25.
- Nikolaenko, V.S. (2015). Analysis tools to ensure the functions of risk management in it projects. The State office. E-Bulletin, 49, 105-120.
- Nikylina, I.E., Tychvatylina, L.R., Cherepanova, N.V. (2009). Modern management. Tomsk Polytechnic University, 235.
- Petukhov, O.N., Nikolaenko, V.S. (2014). Network Projects as a New Paradigm in e-Learning. SGEM 2014 International Multidisciplinary Scientific Conferences on Social Sciences and Arts, 3, 579-586.
- Streles, I.A. (2006). E-economic. Ecsmo, 208.
- The CHAOS Manifesto. (2013). The Standish Group International, 48.
- The CHAOS Manifesto. (2014). The Standish Group International, 16.
Copyright information

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
About this article
Publication Date
20 July 2017
Article Doi
eBook ISBN
978-1-80296-025-9
Publisher
Future Academy
Volume
26
Print ISBN (optional)
Edition Number
1st Edition
Pages
1-1055
Subjects
Business, public relations, innovation, competition
Cite this article as:
Nikolaenko, V. S., & Riatshencev, I. V. (2017). Development Of Organizational Methods For Introduction Of Risk Management In It-Projects. In K. Anna Yurevna, A. Igor Borisovich, W. Martin de Jong, & M. Nikita Vladimirovich (Eds.), Responsible Research and Innovation, vol 26. European Proceedings of Social and Behavioural Sciences (pp. 698-705). Future Academy. https://doi.org/10.15405/epsbs.2017.07.02.90

